Mastering IoT Remote Access With SSH On AWS: A Comprehensive Guide
Hey there, tech enthusiasts! If you're diving into the world of IoT and wondering how to securely access your remote devices using SSH on AWS, you're in the right place. IoT remote access SSH AWS example is more than just a buzzword; it’s a practical solution that can revolutionize how you manage your connected devices. Whether you’re a beginner or an experienced developer, this guide will break down everything you need to know about setting up secure remote access for your IoT devices. So, buckle up and let’s get started!
In today’s interconnected world, IoT devices are everywhere, from smart homes to industrial automation. But with great connectivity comes great responsibility. Ensuring secure access to these devices is crucial, and that’s where SSH on AWS comes into play. This powerful combination allows you to manage your devices remotely without compromising on security. In this article, we’ll explore the ins and outs of IoT remote access with SSH on AWS, including examples and best practices.
Before we dive deep into the technicalities, let’s address the elephant in the room—why should you care about IoT remote access? Well, imagine being able to troubleshoot a device halfway across the globe without lifting a finger. Or think about automating routine tasks without needing physical access. Sounds appealing, right? Let’s uncover the secrets behind this game-changing technology!
Read also:Oshea Jackson Jr From The Streets To The Big Screen
Understanding IoT Remote Access
Let’s kick things off by understanding what IoT remote access really means. Simply put, it’s the ability to control and interact with IoT devices from anywhere in the world. Whether it’s monitoring sensors, updating firmware, or troubleshooting issues, remote access empowers you to do it all without being physically present. And when you combine this with SSH on AWS, you’re talking about a level of security and scalability that’s hard to beat.
Why SSH Is the Key to Secure IoT Access
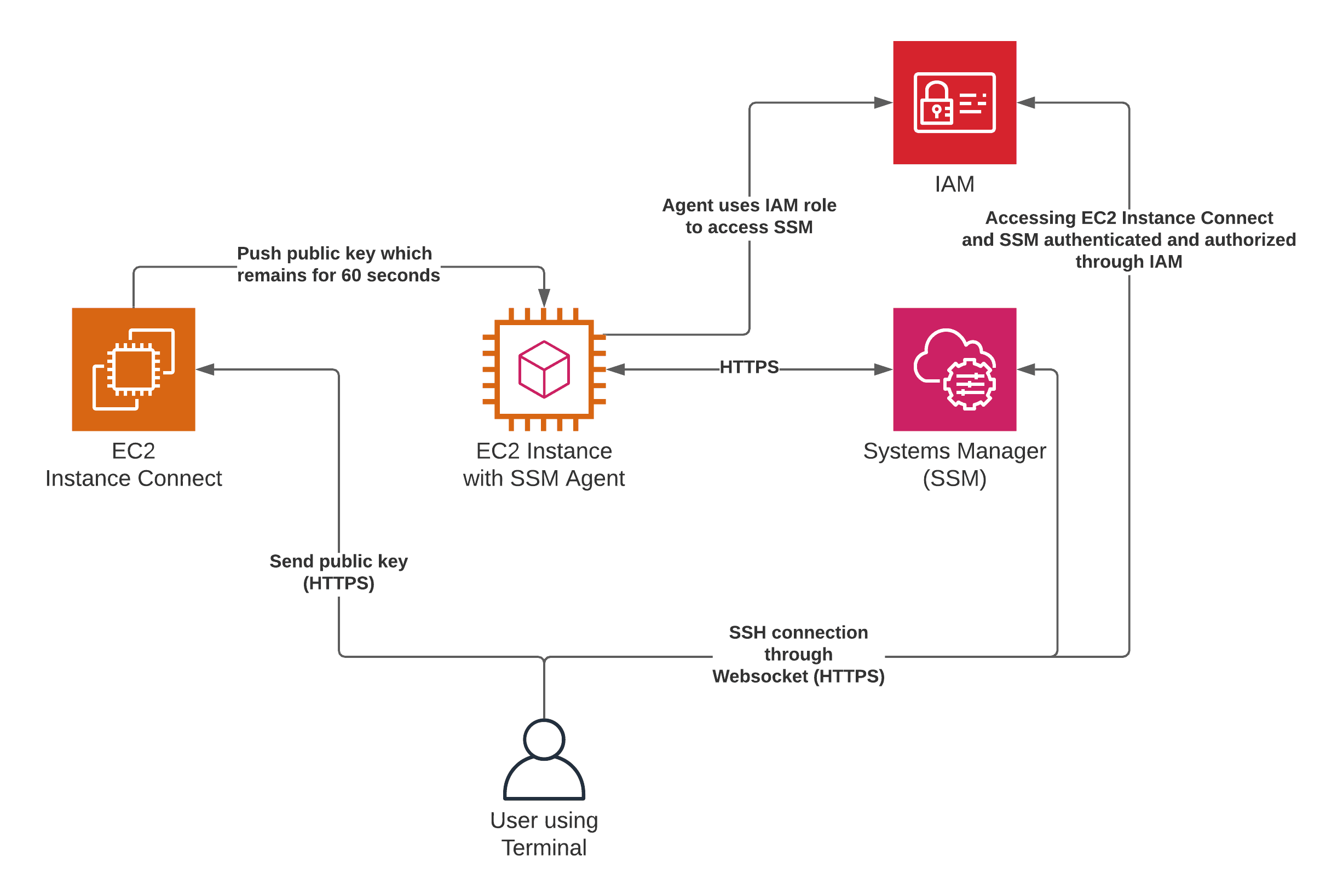
SSH, or Secure Shell, is like the bouncer at a club—it ensures only authorized users can gain access. When you use SSH for IoT remote access, you’re adding a layer of encryption that protects your data and devices from unauthorized access. But here’s the kicker—SSH alone isn’t enough. That’s where AWS comes in.
AWS provides the infrastructure and tools needed to scale your IoT deployments while maintaining top-notch security. Together, SSH and AWS create a formidable duo that ensures your IoT devices are both accessible and protected.
Setting Up IoT Remote Access with SSH on AWS
Now that you understand the basics, let’s get our hands dirty and set up IoT remote access with SSH on AWS. This process involves several steps, but don’t worry—we’ll walk you through each one.
Step 1: Creating an AWS Account
First things first, you’ll need an AWS account. If you don’t have one yet, head over to the AWS website and sign up. Once you’re logged in, navigate to the AWS Management Console. This is where you’ll manage all your IoT resources.
Step 2: Configuring IoT Core
AWS IoT Core is the heart of your IoT setup. It allows devices to securely interact with cloud applications and other devices. To configure IoT Core, follow these steps:
Read also:Foxy Alex The Rising Star Whos Taking The World By Storm
- Log in to the AWS Management Console.
- Navigate to the IoT Core service.
- Create a new thing (a representation of your IoT device).
- Download the certificate and private key for your device.
Step 3: Installing SSH on Your IoT Device
Next, you’ll need to install SSH on your IoT device. This process varies depending on the device’s operating system, but most Linux-based devices come with SSH pre-installed. If not, you can install it using a package manager like apt or yum.
Step 4: Configuring SSH Access
Once SSH is installed, you’ll need to configure it to allow remote access. This involves editing the SSH configuration file (usually located at /etc/ssh/sshd_config) and restarting the SSH service. Be sure to disable password authentication and use key-based authentication for added security.
Best Practices for IoT Remote Access
Now that you’ve set up IoT remote access with SSH on AWS, let’s talk about best practices. These tips will help you maintain a secure and efficient setup:
- Use strong, unique keys for SSH authentication.
- Regularly update your devices’ firmware and software.
- Monitor access logs for suspicious activity.
- Limit access to trusted IP addresses if possible.
IoT Remote Access SSH AWS Example
To give you a better idea of how this works in practice, let’s walk through an example. Imagine you have a fleet of IoT devices deployed across multiple locations. You need to update their firmware remotely without compromising security. Here’s how you can do it:
- Create a new thing in AWS IoT Core for each device.
- Install SSH on each device and configure it for remote access.
- Use AWS IoT Core to send commands to the devices, triggering the firmware update process.
- Monitor the update process and ensure all devices are successfully updated.
Scaling Your IoT Deployment
As your IoT deployment grows, managing individual devices can become cumbersome. That’s where AWS IoT Core’s device management capabilities come in. You can use bulk operations to manage multiple devices at once, saving you time and effort.
Security Considerations
Security should always be at the forefront of your mind when dealing with IoT remote access. Here are some key considerations:
- Use encryption for all communication between devices and the cloud.
- Regularly audit your security settings and update them as needed.
- Implement role-based access control to limit who can access what.
Using AWS IAM for Access Management
AWS IAM (Identity and Access Management) is a powerful tool for managing access to your AWS resources. By creating roles and policies, you can ensure that only authorized users can access your IoT devices. This adds an extra layer of security to your setup.
Monitoring and Troubleshooting
Once your IoT remote access setup is up and running, it’s important to monitor it regularly. AWS IoT Core provides robust monitoring tools that allow you to track device activity and detect potential issues. If something goes wrong, you can use SSH to troubleshoot and resolve the problem remotely.
Common Issues and Solutions
Here are some common issues you might encounter and how to solve them:
- Connection Problems: Check your network settings and ensure your device is connected to the internet.
- Authentication Errors: Verify that your SSH keys are correctly configured and that password authentication is disabled.
- Performance Issues: Optimize your device’s resources and ensure it’s running the latest firmware.
Future Trends in IoT Remote Access
The world of IoT is constantly evolving, and remote access is no exception. Here are some trends to watch out for:
- Increased adoption of edge computing for faster processing.
- Advancements in AI and machine learning for smarter device management.
- Greater emphasis on security and privacy as more devices become connected.
Staying Ahead of the Curve
To stay ahead in the IoT game, it’s important to keep learning and adapting. Follow industry blogs, attend conferences, and experiment with new technologies. The more you know, the better equipped you’ll be to tackle the challenges of tomorrow.
Conclusion
And there you have it—a comprehensive guide to IoT remote access with SSH on AWS. From setting up your devices to monitoring and troubleshooting, we’ve covered everything you need to know to get started. Remember, security is key, so always follow best practices and stay vigilant.
Now it’s your turn to take action! Whether it’s setting up your first IoT device or exploring new ways to optimize your existing setup, the possibilities are endless. Share your thoughts and experiences in the comments below, and don’t forget to check out our other articles for more insights into the world of IoT.
Thanks for reading, and happy hacking!
Table of Contents
- Understanding IoT Remote Access
- Why SSH Is the Key to Secure IoT Access
- Setting Up IoT Remote Access with SSH on AWS
- Best Practices for IoT Remote Access
- IoT Remote Access SSH AWS Example
- Scaling Your IoT Deployment
- Security Considerations
- Using AWS IAM for Access Management
- Monitoring and Troubleshooting
- Future Trends in IoT Remote Access
Article Recommendations