Access IoT SSH AWS: Your Ultimate Guide To Secure Remote Connections
Ever wondered how to securely access IoT devices through SSH on AWS? Well, buckle up because we’re diving deep into this topic. Accessing IoT devices via SSH on AWS isn’t just about connecting; it’s about doing it right, fast, and secure. Whether you're a tech enthusiast or a seasoned developer, this guide has got your back. Let’s explore the ins and outs of remote IoT device management using AWS’s robust infrastructure.
Let’s face it—IoT devices are everywhere these days. From smart homes to industrial automation, IoT is revolutionizing the way we interact with technology. But here’s the kicker: managing these devices remotely can be a real pain if you don’t know what you’re doing. That’s where SSH (Secure Shell) and AWS come into play. Together, they form a powerful duo for secure and efficient IoT management.
In this article, we’ll break down everything you need to know about accessing IoT devices via SSH on AWS. From setting up your environment to troubleshooting common issues, we’ve got all the bases covered. So, grab a coffee, sit back, and let’s get started!
Read also:Understanding Entergy A Comprehensive Guide To Energy Solutions
Table of Contents
- Introduction to Access IoT SSH AWS
- What is IoT and Why Does It Matter?
- Understanding SSH: The Basics
- AWS IoT Core: The Backbone of IoT Management
- Setting Up IoT Devices for SSH Access on AWS
- Ensuring Security in IoT SSH Connections
- Best Practices for Accessing IoT Devices via SSH
- Troubleshooting Common Issues
- Real-World Use Cases of IoT SSH AWS
- Wrapping It Up: Your Next Steps
Introduction to Access IoT SSH AWS
So, you’ve heard the buzzwords—IoT, SSH, and AWS—but what do they really mean when put together? Accessing IoT devices via SSH on AWS allows you to manage and monitor your devices remotely with ease. It’s like having a remote control for your entire IoT infrastructure.
Here’s the deal: IoT devices generate tons of data, and managing them manually can be overwhelming. SSH provides a secure channel for communication, while AWS offers the scalability and reliability needed to handle large-scale IoT deployments. Together, they create a seamless experience for developers and businesses alike.
But why should you care? Well, if you’re looking to streamline your IoT operations, reduce costs, and enhance security, then mastering this setup is a no-brainer. Let’s dig deeper into the world of IoT, SSH, and AWS.
What is IoT and Why Does It Matter?
IoT, or the Internet of Things, refers to the network of physical devices embedded with sensors, software, and connectivity. These devices collect and exchange data, enabling smarter decision-making and automation. Think smart thermostats, wearable health trackers, and even self-driving cars.
But why does IoT matter? In today’s fast-paced world, businesses need real-time insights to stay competitive. IoT devices provide that edge by delivering actionable data. However, managing these devices at scale can be challenging. That’s where SSH and AWS come in.
Key Benefits of IoT
- Improved efficiency and productivity
- Enhanced data collection and analysis
- Cost savings through automation
- Increased customer satisfaction
Understanding SSH: The Basics
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication between devices. It’s like a secret tunnel that lets you access remote systems without exposing sensitive information. SSH uses encryption to protect data during transmission, making it a go-to choice for secure remote access.
Read also:Unveiling The Enigmatic Character Miss Kenworthy Of Bridgerton
When it comes to IoT devices, SSH plays a crucial role in ensuring secure connections. Whether you’re troubleshooting a device or updating its firmware, SSH provides a reliable and secure way to interact with your IoT infrastructure.
How Does SSH Work?
Here’s a quick breakdown:
- Establishes a secure connection between the client and server
- Encrypts all data transmitted between the two
- Authenticates users to prevent unauthorized access
AWS IoT Core: The Backbone of IoT Management
AWS IoT Core is a fully managed service that allows you to connect, monitor, and manage billions of IoT devices. It’s like the nervous system of your IoT ecosystem, enabling seamless communication between devices and the cloud.
With AWS IoT Core, you can:
- Securely connect devices to the cloud
- Process and analyze device data in real-time
- Integrate with other AWS services for enhanced functionality
But what makes AWS IoT Core stand out? Its scalability, reliability, and security features make it an ideal choice for businesses of all sizes. Plus, it integrates seamlessly with SSH, making remote device management a breeze.
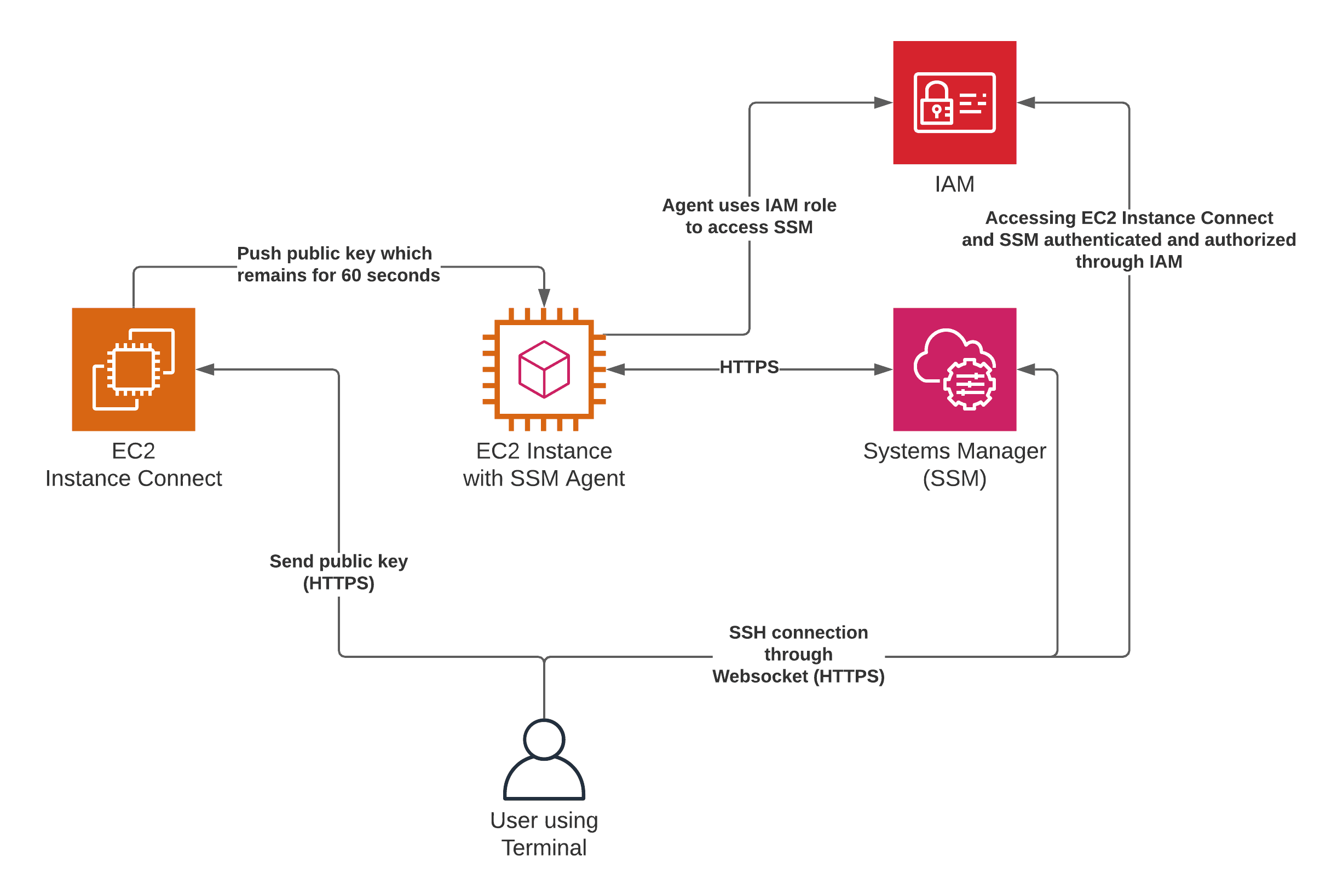
Setting Up IoT Devices for SSH Access on AWS
Setting up IoT devices for SSH access on AWS might sound intimidating, but trust me, it’s easier than you think. Follow these steps to get started:
Step 1: Prepare Your Environment
Make sure you have the following:
- An AWS account
- An IoT device with SSH capabilities
- A computer with SSH client installed
Step 2: Create an AWS IoT Thing
Head over to the AWS Management Console and create a new IoT thing. This will serve as the digital representation of your physical device.
Step 3: Configure SSH on Your Device
Enable SSH on your IoT device and generate a key pair for authentication. This ensures that only authorized users can access the device remotely.
Step 4: Connect Your Device to AWS IoT Core
Use the AWS IoT Device SDK to connect your device to AWS IoT Core. This will allow you to manage the device from the cloud.
Step 5: Test Your Setup
Use an SSH client to connect to your device and verify that everything is working as expected. If you encounter any issues, refer to the troubleshooting section below.
Ensuring Security in IoT SSH Connections
Security should always be your top priority when dealing with IoT devices. Here are some tips to keep your SSH connections secure:
- Use strong, unique passwords and key pairs
- Enable two-factor authentication whenever possible
- Regularly update your devices and software
- Monitor your connections for suspicious activity
Remember, a single breach can compromise your entire IoT infrastructure. By following these best practices, you can significantly reduce the risk of unauthorized access.
Best Practices for Accessing IoT Devices via SSH
Now that you know how to set up SSH access for IoT devices on AWS, let’s talk about some best practices to ensure smooth and secure operations:
1. Automate Routine Tasks
Use scripts and automation tools to handle repetitive tasks like firmware updates and configuration changes. This saves time and reduces the risk of human error.
2. Monitor Device Health
Regularly check the status of your devices and address any issues promptly. AWS IoT Core provides built-in monitoring tools to help you stay on top of things.
3. Document Everything
Keep detailed records of your setup process, including device configurations and key pairs. This will come in handy if you need to troubleshoot or onboard new team members.
4. Stay Updated
Keep an eye on the latest developments in IoT, SSH, and AWS. Technology evolves rapidly, and staying informed is key to maintaining a secure and efficient IoT infrastructure.
Troubleshooting Common Issues
Even with the best preparation, things can go wrong. Here are some common issues you might encounter and how to fix them:
Issue 1: Unable to Connect via SSH
Check your firewall settings and ensure that SSH is enabled on your device. Also, verify that your key pair is correct and hasn’t expired.
Issue 2: Slow Connection Speeds
Optimize your network configuration and consider using a faster internet connection. Additionally, ensure that your device has enough processing power to handle SSH connections.
Issue 3: Security Alerts
Investigate any security alerts immediately and take appropriate action. This might involve updating your device firmware, changing passwords, or revoking compromised key pairs.
Real-World Use Cases of IoT SSH AWS
Let’s look at some real-world examples of how businesses are leveraging IoT SSH AWS:
1. Smart Agriculture
Farmers use IoT sensors to monitor soil moisture and weather conditions. By accessing these devices via SSH on AWS, they can make data-driven decisions to optimize crop yields.
2. Industrial Automation
Manufacturers rely on IoT devices to monitor production lines and identify bottlenecks. SSH access on AWS allows them to troubleshoot issues remotely and minimize downtime.
3. Smart Cities
Cities use IoT devices to manage traffic flow, energy consumption, and public safety. SSH on AWS provides a secure and scalable platform for managing these devices at scale.
Wrapping It Up: Your Next Steps
Accessing IoT devices via SSH on AWS is a game-changer for businesses looking to streamline their IoT operations. By following the steps outlined in this guide, you can set up a secure and efficient remote access system for your IoT devices.
Here’s a quick recap of what we’ve covered:
- Understanding the basics of IoT, SSH, and AWS
- Setting up IoT devices for SSH access on AWS
- Ensuring security and following best practices
- Troubleshooting common issues
- Exploring real-world use cases
Now it’s your turn to take action. Whether you’re just starting out or looking to enhance your existing setup, this guide provides the tools and knowledge you need to succeed. So, what are you waiting for? Get out there and start building your IoT empire!
Oh, and don’t forget to leave a comment or share this article with your friends. Together, we can make the world a smarter, more connected place. Cheers!
Article Recommendations