Securely Connect VPC Network: A Must-Have Skill For Modern Cloud Architects
Hey there, tech enthusiast! If you've ever wondered how to securely connect VPC networks in the cloud, you're in the right place. This guide will walk you through everything you need to know about creating airtight connections for your virtual private cloud (VPC) environments. Whether you're a seasoned pro or just starting out, this article has got your back!
Let's face it, the cloud can be a wild frontier, and securing your VPC network is like building a fortress in cyberspace. With cyber threats lurking around every corner, understanding how to lock down your VPC connections isn't just an option—it's a necessity. In this article, we'll dive deep into the nitty-gritty of securely connecting VPC networks, so you can protect your data like a pro.
But hold up! Before we get into the juicy details, let's take a moment to appreciate why securing VPC networks is such a big deal. In today's digital landscape, businesses rely heavily on cloud infrastructure, and a single breach could mean disaster. That's why mastering this skill is not only important but also a game-changer for your career. Let's roll up our sleeves and get started!
Read also:Adam Driver Dating History A Closer Look At Love And Relationships
What is a VPC Network Anyway?
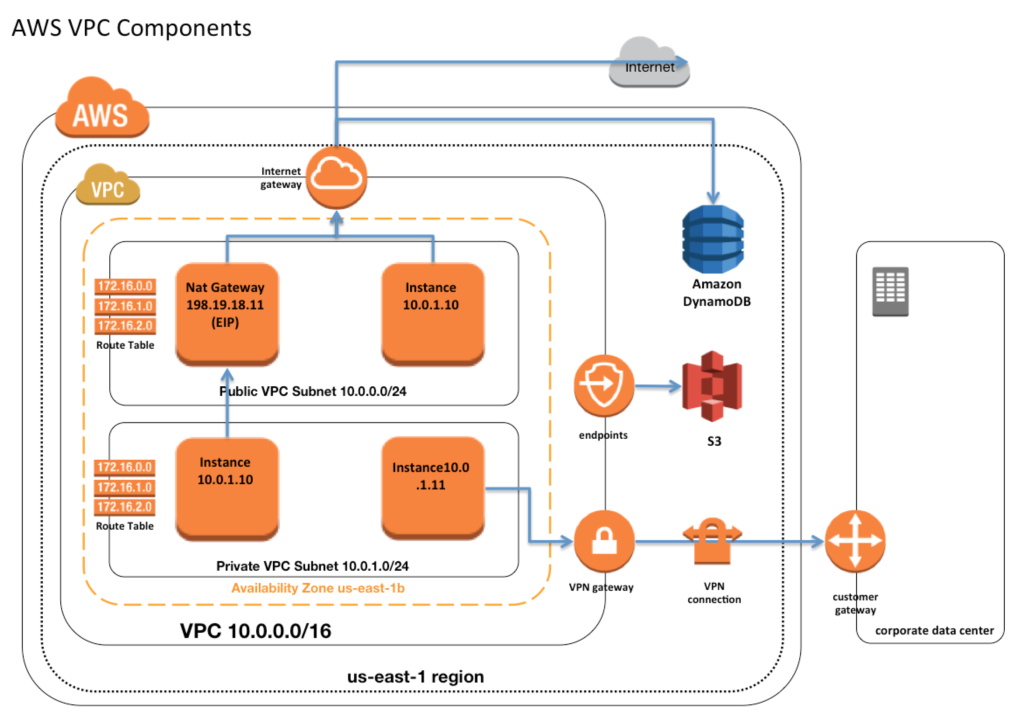
Alright, let's break it down. A VPC (Virtual Private Cloud) network is essentially your own private network in the cloud. Think of it as your personal playground where you can launch resources like EC2 instances, databases, and more without worrying about the outside world peeking in. But here's the catch—just because it's private doesn't mean it's secure. You gotta put in the work to make sure it stays that way.
Now, why do we need to securely connect VPC networks? Well, imagine your VPC as an island, and you need bridges to connect it to other islands or the mainland. Those bridges are your connections, and if they're not secure, bad actors can waltz right in and cause chaos. So, yeah, securing those connections is kind of a big deal.
Key Features of a VPC Network
Let's talk about what makes a VPC network so special:
- **Isolation**: Your VPC lives in its own little bubble, separate from the public internet unless you say otherwise.
- **Customizable Subnets**: You can carve up your VPC into smaller chunks called subnets, each with its own rules and restrictions.
- **Security Groups and ACLs**: These are like bouncers at a club, deciding who gets in and who stays out.
- **Private and Public IPs**: You can assign private IPs for internal communication and public IPs for external access.
These features give you the flexibility to design a network that fits your specific needs. But remember, with great power comes great responsibility. You've gotta know how to use these tools to keep your VPC safe.
Why Securely Connect VPC Network Matters
Here's the deal—data breaches are no joke. According to a report by IBM, the average cost of a data breach in 2022 was a whopping $4.35 million. That's a lot of moolah! And guess what? A lot of those breaches happen because of poorly secured network connections. So, yeah, securing your VPC network isn't just about protecting your data; it's about protecting your business's bottom line.
But it's not all about money. Think about your customers. If their data gets compromised because of a weak VPC connection, their trust in your business could be shattered. And trust me, regaining trust is way harder than keeping it in the first place. So, securing your VPC network is not only a technical necessity but also a moral obligation.
Read also:Who Is Patrick Mahomes Father And What Makes Him Stand Out
Steps to Securely Connect VPC Network
Alright, let's get down to business. Here's how you can securely connect your VPC network:
Step 1: Understand Your Network Requirements
Before you start setting up connections, you need to know what you're working with. Ask yourself these questions:
- How many VPCs do I need to connect?
- What kind of traffic will be flowing between them?
- Do I need internet access for any of my resources?
Answering these questions will help you design a network architecture that meets your specific needs.
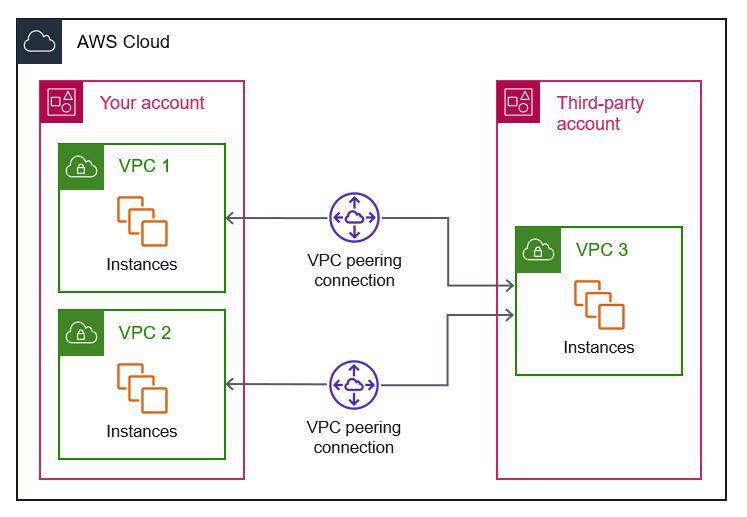
Step 2: Set Up VPC Peering Connections
VPC peering is like creating a direct line of communication between two VPCs. It allows resources in different VPCs to communicate with each other as if they were in the same network. Here's how you do it:
- Create a peering connection request from one VPC to another.
- Accept the request on the other side.
- Update your route tables to include the peering connection.
Easy peasy, right? Just remember, VPC peering connections don't support transitive peering, so if you need to connect more than two VPCs, you'll need to set up multiple peering connections.
Step 3: Use AWS Transit Gateway
If you're dealing with a lot of VPCs, managing multiple peering connections can get messy. That's where AWS Transit Gateway comes in. It acts as a central hub for all your VPC connections, making it easier to manage and scale your network.
Here's how you can set it up:
- Create a transit gateway in the AWS Management Console.
- Attach your VPCs to the transit gateway.
- Update your route tables to use the transit gateway.
With AWS Transit Gateway, you can connect up to thousands of VPCs with just a few clicks. Plus, it supports transitive routing, so you don't have to worry about setting up multiple peering connections.
Best Practices for Securing VPC Connections
Now that you know how to connect VPC networks, let's talk about how to keep them secure. Here are some best practices to follow:
1. Use Network Access Control Lists (ACLs)
Network ACLs act as a firewall for your subnets, controlling inbound and outbound traffic at the subnet level. Here's how you can use them:
- Create a network ACL for each subnet.
- Define rules for allowing or denying traffic.
- Associate the network ACL with your subnet.
By using network ACLs, you can add an extra layer of security to your VPC connections.
2. Implement Security Groups
Security groups are like virtual firewalls for your instances, controlling traffic at the instance level. Here's how to use them:
- Create a security group for each application or service.
- Define rules for allowing or denying traffic.
- Assign the security group to your instances.
Security groups work in tandem with network ACLs to provide comprehensive protection for your VPC connections.
3. Enable VPC Flow Logs
VPC Flow Logs help you monitor traffic going in and out of your VPC. Here's how you can enable them:
- Go to the VPC Dashboard in the AWS Management Console.
- Select the VPC you want to monitor.
- Click on "Create Flow Log" and configure your settings.
By enabling VPC Flow Logs, you can detect and respond to suspicious activity in your network.
Common Challenges and How to Overcome Them
Let's talk about some common challenges you might face when securely connecting VPC networks and how to overcome them:
Challenge 1: Managing Multiple Peering Connections
If you're dealing with a lot of VPCs, managing multiple peering connections can get overwhelming. The solution? Use AWS Transit Gateway. It simplifies the process by acting as a central hub for all your VPC connections.
Challenge 2: Ensuring High Availability
High availability is crucial for mission-critical applications. To ensure high availability, you can use AWS Direct Connect to establish a dedicated network connection between your on-premises network and your VPC. This reduces latency and improves reliability.
Challenge 3: Monitoring Network Traffic
Monitoring network traffic can be a daunting task, especially if you're dealing with a large number of VPCs. The solution? Use AWS CloudWatch and VPC Flow Logs to monitor and analyze your network traffic in real-time.
Tools and Technologies for Securing VPC Connections
Here are some tools and technologies you can use to secure your VPC connections:
1. AWS Shield
AWS Shield protects your VPC connections from DDoS attacks. It's available in two tiers: Standard and Advanced. The Standard tier is included with AWS, while the Advanced tier offers enhanced protection and support.
2. AWS WAF
AWS WAF helps you protect your web applications from common web exploits. You can use it to block SQL injection and cross-site scripting attacks, ensuring your VPC connections remain secure.
3. AWS CloudTrail
AWS CloudTrail helps you monitor API activity in your AWS account. By tracking changes to your VPC configurations, you can quickly identify and respond to unauthorized changes.
Real-World Examples of Secure VPC Connections
Let's take a look at some real-world examples of how companies are using secure VPC connections:
Example 1: Netflix
Netflix uses AWS to deliver its streaming service to millions of users around the world. To ensure secure VPC connections, they use a combination of VPC peering and AWS Transit Gateway to connect their global network of data centers.
Example 2: Airbnb
Airbnb relies on AWS to power its platform, and secure VPC connections are a critical part of their infrastructure. They use network ACLs and security groups to control traffic and protect sensitive data.
Example 3: Slack
Slack uses AWS to deliver its collaboration platform to businesses of all sizes. To ensure secure VPC connections, they use AWS Shield and AWS WAF to protect against DDoS attacks and web exploits.
Future Trends in VPC Security
As technology continues to evolve, so does the field of VPC security. Here are some trends to watch out for:
Trend 1: Zero Trust Architecture
Zero Trust Architecture is all about verifying everything and trusting nothing. It's a paradigm shift in how we think about security, and it's gaining traction in the cloud space. Expect to see more companies adopting Zero Trust principles for their VPC connections.
Trend 2: AI-Powered Security
AI is revolutionizing the field of cybersecurity, and VPC security is no exception. AI-powered tools can analyze vast amounts of data to detect and respond to threats in real-time, making it easier to secure VPC connections.
Trend 3: Edge Computing
Edge computing is all about processing data closer to the source, reducing latency and improving performance. As more companies adopt edge computing, expect to see new challenges and opportunities in securing VPC connections.
Conclusion
And there you have it, folks! A comprehensive guide to securely connecting VPC networks. From understanding the basics to implementing best practices, we've covered everything you need to know to protect your VPC connections like a pro.
But remember, securing your VPC network is an ongoing process. As threats evolve, so should your security measures. So, keep learning, keep experimenting, and most importantly, keep your VPC connections secure.
Before you go, don't forget to drop a comment and let us know what you think. And if you found this article helpful, feel free to share it with your friends and colleagues. Until next time, stay secure and keep hacking!
Table of Contents
Article Recommendations